
Edited article reproduced with the permission of Microsoft. Scan the QR code for the full report.

Over the past year, the world has borne witness to a burgeoning cybercrime economy. We’ve seen the cyberattack landscape becoming increasingly sophisticated as cybercriminals continue – and escalate – their activity in times of crisis. New levels of supply chain and ransomware attacks were a powerful reminder that we must all work together and in new ways to protect the cybersecurity of the planet.
Recently we have seen two positive trends. First, more governments and companies are coming forward when they are victims. This transparency has made it clear to governments around the world that cybercrime is a threat to security. Second, now that governments worldwide recognise that cybercrime is a threat to national security, combatting it is a priority.
RISING THREATS
Microsoft sees four critical threats growing in sophistication and scale.
Ransomware and extortion is a high-profit, low-cost business that can debilitate targeted organisations. A ransomware and extortion attack involves a threat actor deploying malware that encrypts and steals data and then holds that data for ransom, often demanding payment in cryptocurrency. A global collaboration between the private sector, law enforcement and government is required to counter ransomware. This collaboration can reduce the profitability of this crime, increase the risk for criminals, and supply victims with practical tools for efficient prevention and remediation. Microsoft is a contributor to the Ransomware Task Force report, a comprehensive framework designed to combat ransomware.
Phishing is the most common type of malicious email observed in our threat signals.
These malicious emails trick an individual into sharing sensitive information, such as usernames and passwords. To do this, attackers craft emails using a variety of themes, such as productivity tools, password resets or other notifications with a sense of urgency to lure a user into clicking on a link.
The number of phishing emails observed in Microsoft Exchange global mail flow increased from June 2020 through June 2021. Microsoft saw a pronounced surge in November potentially related to holiday-themed phishing and a subsequent decrease over the US winter holidays, potentially indicating that
attackers send fewer messages when many people are not working.

Malware is another example of how threat actors utilise emails for their objectives. Various malware variants such as Agent Tesla, IcedID, Trickbot and Qakbot use email as a primary distribution method. These emails will use links or attachments to deliver malware and often use techniques that overlap with phishing emails. The malware, once triggered, can be used to manipulate applications and services in the victim’s network to disrupt or infiltrate their systems.
Between July 2020 and June 2021,Microsoft observed an overall downward trend in the number of emails containing malware, despite an initial surge. The decrease is associated with the industry successfully taking down malware variants. Microsoft took down the Trickbot malware.
Browser results manipulation is a rising threat using web code to alter the results returned by a browser. These altered results encourage the victim to install malware or provide sensitive data. Throughout 2021 Microsoft saw an average of 180,000, up from 77,000, browser manipulation encounters per month.
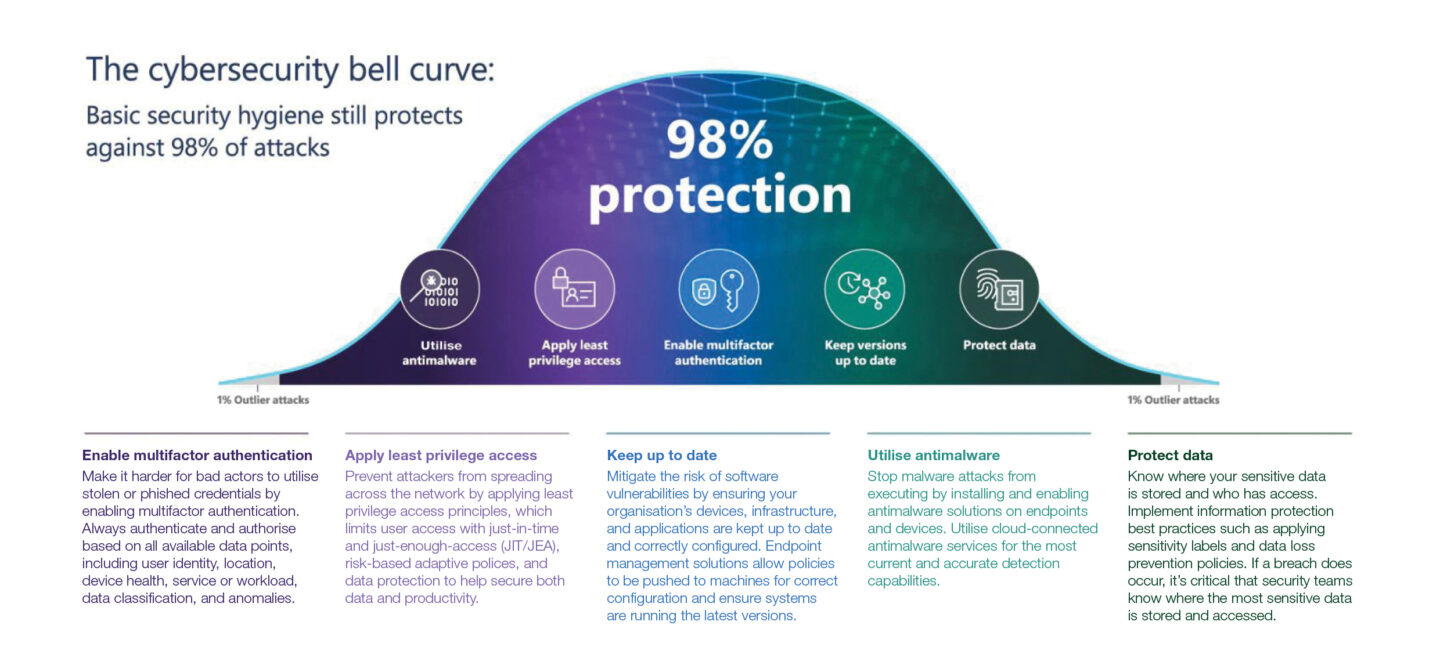
RECOMMENDATIONS
Several vital themes arise throughout the different sections of this report (available at https://aka.ms/MDDR) that Microsoft encourages you to consider as you think about improving your security posture:
Do the basics well
Although attackers are becoming more sophisticated, good cyber hygiene and basic security measures are often the best way to disrupt, prevent and detect their attacks.
Take a holistic view
Organisational structure and silos must not drive how we organise security and risk. Attackers will look for vulnerabilities across these silos, so we need to consider risk at an organisational level. It would be best if you standardised approaches across the different teams in an organisation. It also underlines the importance of standards as we seek to harmonise between companies, which is increasingly important to managing supply chain risk.
Any element can be used as an attack vector
Attackers will look for the weakest link across an organisation’s ecosystem, so we must manage it holistically. The weakest link may be a connected freezer or building management system used to gain access to the corporate network, or it may be a user or device that is compromised via a phishing email to gain access to the operational technology running a factory or production plant. We need to consider and manage the organisation’s entire attack surface.
Think about people
People engage with technology and are often used as a way of gaining access to the digital environment. Think about how to engage with them in a way that will help them to understand the risks they face. Understanding, engaging and educating people will allow them to become a critical line of defence against modern threats, whether that is misinformation seeking to influence decisions and undermine democracy or phishing emails seeking to gain access to and compromise an
organisation’s digital assets.
Zero Trust is an architectural principle
The threats Microsoft has seen underline the importance of Zero Trust in designing and managing the risk in an organisation. The last year has emphasised why there should be no such thing as a trusted application, trusted user or trusted device with unrestricted access. The risk and context of every connection needs to be considered before allowing access to resources. Zero Trust is not a technology but an approach to managing risk. When implemented correctly, it can enable us to unlock the potential of modern technology while limiting our exposure in a hyperconnected world.

At Linfox, cybersecurity is everyone’s responsibility.
Even with the most advanced technologies, Linfox people are the first line of defence against these threats. Regular team member training ensures everyone is aware of the risks and common types of attack. In addition, frequent alerts convey the latest forms of phishing emails and text messages to our people.
As a part of Australia’s critical infrastructure, Linfox works closely with the Australian Cyber Security Centre (ACSC). We have completed the government’s Infosec Registered Assessor’s Program (IRAP) assessment, and focus on the ‘Essential 8’ mitigation strategies the ACSC recommend.
Linfox conducts cyberattack exercises with key partner CyberCX and the learnings inform our cyber plans. As a highly connected enterprise, Linfox partners with Telstra to further segment our network for additional protection for our many customers and partners.
Crucially, Linfox has a business-led critical incident response framework at the ready to manage the consequences of a cyberattack. As cyber threats continue to evolve, Linfox is working smarter to stay ahead of the risk.

